OBT Synergy can Help You
Navigate the Cyber-security Minefield
Every phone, tablet, laptop and desktop connected to the internet
is an opportunity for hackers and scammers to make money for themselves

Hi, I'm Clive. and have over 20 year's experience in protecting business data and systems.
My data security model was recommended to the BAE Systems Board, to be used for all divisions and projects world-wide, by their Security Auditors.
I also advise on how to protect secret projects for high net worth individuals.
Your security is only as strong as the weakest link in your chain

Discover why we must take cyber-crime seriously
Our personal security is at risk from the weakest link in our chain of connections and apps.
There are ways to check safely - where your emails, passwords, credit card and other personal details are probably for sale to hackers on the dark web, as you read this.
Hundreds of research studies by the security industry show people are not taking simple steps to protect themselves from viruses, phishing, ransomware and malware.
How we help hackers - to make our life harder
Your phones, tablets, laptops and desktops are already being used by hackers
Your devices are being used to attack company websites with a millions of requests to stop them working. This is called a DDoS (Distributed Denial of Service) attack.
This happens in the background without your knowledge and is not picked up as threats by Anti-virus or Malware protection.
Your device is easily hi-jacked to use your processing power and internet connection, to launch DDoS attacks. The recent DDoS attack on Amazon was from millions of people's devices.
Why the Internet of Things is a hackers paradise
The Internet of Things (IoT) are smart devices which interact, with other devices over the internet. They work by granting remote access to a user for managing the device.
It is predicted there will be 3 smart devices for every person on the planet by 2021
Stop for a few minutes and count how many smart devices you have....
Smart controllers like
Amazon Echo
Google Home Voice
Apple Siri
Mobile phones
Smart watches
Central heating controls
Universal remote controllers
Smart devices like
Doorbells
Security cameras
Bulbs and lighting systems
Temperature Controls
Locks
Smoke Alarms
Smart plugs
Smart devices like
Children's interactive toys
Amazon Dash button
Fitness trackers
Kuri mobile robot
TVs
Speakers
Air quality monitors
Smart Wi-Fi and Bluetooth devices are all ways which allow hackers into your network.
It is like locking your front door and leaving all your windows open
Once inside your Wi-Fi or Bluetooth network - hackers can gain access to all your connected devices, including your phone and laptop.
Simple security actions will give you peace of mind and can save you thousands
You worked hard to earn what you have. Don't give it away by making a small mistake.
Why cyber-security advice is a challenge?
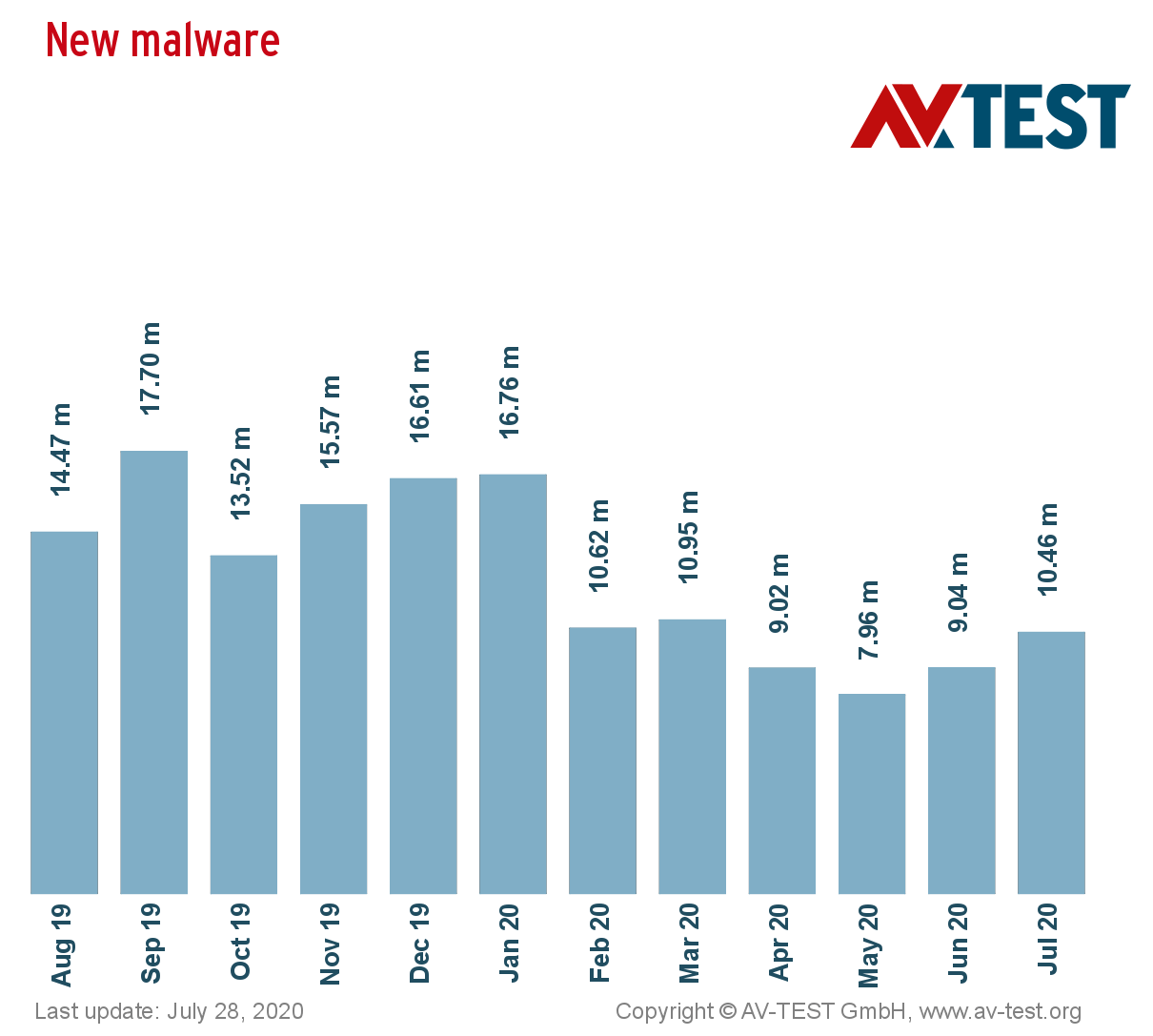
The Independent IT-Security Institute
has identified an average of 10,666,000 new malware items per month this year.
In addition there are thousands of new email phishing scams every day.
Keep in mind:
Scammers are always 7 days ahead of security fixes and public awareness of what they are doing
Which makes it impossible to keep yourself secure.
Many Banks, Media and Organisations are providing outdated cyber-security advice because
- Anti-virus can only protect from known threats
- The amount of information is overwhelming and it is targeted at a wide audience.
- Nobody can keep up with the new scams appearing every day
Lack of knowledge gives hackers and scammers a golden opportunity to exploit individuals and companies of all sizes.
If Security Professionals can't keep up with changes, how can we protect ourselves?
There are simple ways to make sure everyone is better protected
Examples of how people are tricked!
Most of us know someone who has lost money to fraud or hacking.
The insurance industry statistics show 50% of businesses were hacked last year.
Hacks on individuals and small companies are not in the public domain, because only the top branded companies make the news.
Hackers look for options to attack easy targets and don't care who they hurt.
- They exploit both human misery like Covid-19 and natural disasters
- They also exploit our good nature when we give funds to help disaster victims
While we were all supporting the world wide health services, the hackers were holding hospitals and PPE suppliers to ransom by locking them out of their systems.
Criminals share information to attack us from every direction. Here are just three...
The security industry recently stated there are two scenarios we need to accept
- Those who know they have been hacked
- Those who haven't found out - that they have already been hacked
How do you keep updated on cyber-security risks
that will impact your devices and applications?
There are many ways we pick up information, and we get our news from many different channels.
When was the last time you checked to see, if the news originated from a trusted source?
Is the news you are reading current or old news?
Do you believe information shared on social media?
What TV and news channels do you trust?
Fast timely security updates will protect you!
How would you feel if you were one of these victims?
There are many examples of horror stories of criminal activity
Scam Avoidance Education & Victims Support Unit of the Society of Citizens Against Relationship Scams Inc has Stories of Scams, Online Fraud & Their Traumatized Victims
The Banking & Payments Federation Ireland has stories of Personal Fraud and Business Fraud
An early warning system helps people get expert advice fast and protect themselves
Every day, the AV-TEST Institute registers over 350,000 new malicious programs (malware) and potentially unwanted applications (PUA).
There are security awareness platforms that share the latest phishing email, so we have an early warning system of what to look out for
The Hacking Process Time Line
A hacker will find a security hole in software or a new way to con people
- They test that it works
- Sell it on the dark web to other criminals
- They use emails, mobile apps and software bots to attack
- It could take several days before the security industry picks it up
- Then it takes several more days to fix and update devices
If fixes are not applied then that person is at increasing risk
Cyber-security is far too technical and confusing
Information changes daily, because the number of threats increase every day.
- There is too much confusing information and outdated information can be dangerous
- Not targeted for individuals and it is almost impossible to pick though the minefield of information.
- The biggest challenge is to find reliable sources then to filter out irrelevant information.
- Then to understand the technicalities to make it easy to know what needs to be fixed.
Some large companies provide their employees with security awareness training. It is not extended to their families and friends.
Family and Friends are connected to you as part of your network. This increases your risk.
OBT Synergy are launching
OBT 365 Security Awareness
OBT 365 Personalised Security Awareness Training and Security Digests to help protect you from the latest cyber-security threats.
OBT Synergy has implemented simple solutions to fix technical problems.
Knowledge is power - when you are aware of the dangers, you can reduce your risk.
- 1Identify security knowledge gaps: with our Analysis Questionnaire
- 2Protect yourself: by becoming Cyber Smart
- 3Get Personalised training: to fix the gaps in your security knowledge
- 4Get Personalized alerts: of latest threats on your chosen Apps & devices

What People Are Saying About Our Solution
Since we started with security awaress training we have seen a significant reduction in the number of people clicking malicious links or attachments.
Micro Business CEO
The World's most cost-effective Security Awareness Training
Identifies gaps in your security knowledge because people are the biggest security risk
Personalised training to fill in the missing gaps that you must have to stay safe
Only personalised alert notifications for devices and Apps
Corporate security for micro business and private individuals


100% Satisfaction Guaranteed

Secure Payment
Testimonials to Prove it Works for Real People
This enabled us to rapidly deploy training programmes unique to our security weaknesses. It was great that OBT Synergy managed the reminders and weekly summary reports.
ECS Ltd CEO

Clive Hornsby
Joint Creator of OBT 365
About the Author
Security is only as strong as the weakest link in the chain
Everyone and everything you are connected to is part of that chain.
We are independent and continually assess products and services to ensure our clients use the best in the market. We don’t develop software we have partner relationships with the leading vendors.
Selecting the right software is only the first step. The more important step is how it is implemented within the business to get the maximum productivity gains and the best ROI.
I am already protected and don't need help
All devices connected to the internet are secure, until they are connected to a human.
You will get caught with one or more of these - viruses, phishing, ransomware and malware
It will not happen to me
Most people believe they are safe and it will not happen to them.
We all know of people it has happened to and the cost for victims can easily be thousands.
My Anti-virus protects me
Anti-virus protects from known threats. Anti-virus software cannot stop threats they don't know about.
Macs don't get attacked
Prior to 2015 I would have agreed. As Macs are now more popular they are prime targets for hackers. The average number of Malware applications hacking Macs over the last 3 years is 58,333 per year.
My iPhone has protection
Apple have good security on their phones. They cannot stop human nature where people clicking on links and do things the shouldn't
Advantages vs Disadvantages
Like most things in life there is an up and a down side
The Pros List
The Cons List
Here's "What You Get"

100% Satisfaction Guaranteed

Secure Payment

100% Satisfaction Guarantee
You are fully protected by our 100% Satisfaction-Guarantee. If you don't improve your security protection over 12 months, just let us know and we'll send you a prompt refund.
(This requires a commitment to training and taking action on your personalised alerts.)
Clive Hornsby
Frequently Asked Questions
Why should we believe you?
Will my Anti virus protect me?
Does a VPN protect me?
Why is security a people issue and not IT?
What do I actually need to be safe?
How can I check if my data is for sale?
Can I share this page with Friends?
P.S.: Our security team understands the challenges of keeping updated on the massive amount of threats every day. Working out security impacts from all the technician jargon is another ball game completely.
By taking a small step today and plugging into our security team you can dramatically reduce the odds of being hacked or scammed.
You will get peace of mind knowing you are better equipped to hang onto your hard earned cash.
If you want to go it alone there are no hard feelings and we will part as friends.
Copyright - OBT Synergy Ltd